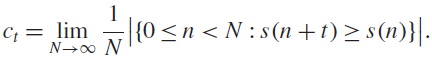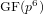Refine search
Actions for selected content:
13 results
The Eigenvalue Method in coding theory
- Part of
-
- Journal:
- Canadian Journal of Mathematics , First View
- Published online by Cambridge University Press:
- 22 September 2025, pp. 1-41
-
- Article
-
- You have access
- Open access
- HTML
- Export citation
A lower bound for Cusick’s conjecture on the digits of n + t
- Part of
-
- Journal:
- Mathematical Proceedings of the Cambridge Philosophical Society / Volume 172 / Issue 1 / January 2022
- Published online by Cambridge University Press:
- 24 February 2021, pp. 139-161
- Print publication:
- January 2022
-
- Article
-
- You have access
- Open access
- Export citation
NONBINARY DELSARTE–GOETHALS CODES AND FINITE SEMIFIELDS
- Part of
-
- Journal:
- Glasgow Mathematical Journal / Volume 62 / Issue S1 / December 2020
- Published online by Cambridge University Press:
- 07 May 2020, pp. S186-S205
- Print publication:
- December 2020
-
- Article
-
- You have access
- Export citation
ISOGENIES OF ABELIAN VARIETIES IN CRYPTOGRAPHY
- Part of
-
- Journal:
- Bulletin of the Australian Mathematical Society / Volume 101 / Issue 3 / June 2020
- Published online by Cambridge University Press:
- 16 March 2020, pp. 508-509
- Print publication:
- June 2020
-
- Article
-
- You have access
- Export citation
On Zeros of a Polynomial in a Finite Grid
- Part of
-
- Journal:
- Combinatorics, Probability and Computing / Volume 27 / Issue 3 / May 2018
- Published online by Cambridge University Press:
- 15 February 2018, pp. 310-333
-
- Article
- Export citation
Collecting relations for the number field sieve in
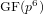 $\text{GF}(p^{6})$
$\text{GF}(p^{6})$
- Part of
-
- Journal:
- LMS Journal of Computation and Mathematics / Volume 19 / Issue A / 2016
- Published online by Cambridge University Press:
- 26 August 2016, pp. 332-350
-
- Article
-
- You have access
- Export citation
Reduced memory meet-in-the-middle attackagainst the NTRU private key
- Part of
-
- Journal:
- LMS Journal of Computation and Mathematics / Volume 19 / Issue A / 2016
- Published online by Cambridge University Press:
- 26 August 2016, pp. 43-57
-
- Article
-
- You have access
- Export citation
Constructing abelian surfaces for cryptography via Rosenhain invariants
- Part of
-
- Journal:
- LMS Journal of Computation and Mathematics / Volume 17 / Issue A / 2014
- Published online by Cambridge University Press:
- 01 August 2014, pp. 157-180
-
- Article
-
- You have access
- Export citation
Explicit Kummer surface formulas for arbitrary characteristic
- Part of
-
- Journal:
- LMS Journal of Computation and Mathematics / Volume 13 / January 2010
- Published online by Cambridge University Press:
- 01 January 2010, pp. 47-64
-
- Article
-
- You have access
- Export citation
Certain Exponential Sums and Random Walks on Elliptic Curves
-
- Journal:
- Canadian Journal of Mathematics / Volume 57 / Issue 2 / 01 April 2005
- Published online by Cambridge University Press:
- 20 November 2018, pp. 338-350
- Print publication:
- 01 April 2005
-
- Article
-
- You have access
- Export citation
Counting irreducible Goppa codes
- Part of
-
- Journal:
- Journal of the Australian Mathematical Society / Volume 71 / Issue 3 / December 2001
- Published online by Cambridge University Press:
- 09 April 2009, pp. 299-306
- Print publication:
- December 2001
-
- Article
-
- You have access
- Export citation
A theta relation in genus 4
-
- Journal:
- Nagoya Mathematical Journal / Volume 161 / March 2001
- Published online by Cambridge University Press:
- 22 January 2016, pp. 69-83
- Print publication:
- March 2001
-
- Article
-
- You have access
- Export citation
Jacobi Sums, Irreducible Zeta-Polynomials, and Cryptography
-
- Journal:
- Canadian Mathematical Bulletin / Volume 34 / Issue 2 / 01 June 1991
- Published online by Cambridge University Press:
- 20 November 2018, pp. 229-235
- Print publication:
- 01 June 1991
-
- Article
-
- You have access
- Export citation